OK, I heard from enough of you that wanted me to do this in PowerShell instead of my batch file. Here is the original article using built-in Windows utilities. This article will show the original batch file converted to PowerShell.
I created four variables. One for the domain name, one for the top-level domain identifier, one to determine if you want the OUs protected from accidental deletion, and the last to hold the initial password as a secure string.
The structure of the script is the same as the original batch file:
- Creates the OUs
- Creates the security groups
- Creates the user accounts
- Adds the user accounts into the security groups
- Creates the computer accounts
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 | $ADDomain = "labaddomain"$TLD = "com"$Protect = $False$CryptoPwd = (ConvertTo-SecureString -AsPlainText "FakePwd" -Force)#Create OUsNew-ADOrganizationalUnit -Name "Lab" `-Path "dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion $Protect -verboseNew-ADOrganizationalUnit -Name "Accounts" `-Path "ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion $Protect -verboseNew-ADOrganizationalUnit -Name "Admin" `-Path "ou=Accounts,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion $Protect -verboseNew-ADOrganizationalUnit -Name "Service" `-Path "ou=Accounts,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion $Protect -verboseNew-ADOrganizationalUnit -Name "User" `-Path "ou=Accounts,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion $Protect -verboseNew-ADOrganizationalUnit -Name "Desktops" `-Path "ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion $Protect -verboseNew-ADOrganizationalUnit -Name "Admin" `-Path "ou=Desktops,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion $Protect -verboseNew-ADOrganizationalUnit -Name "XD76" `-Path "ou=Desktops,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion $Protect -verboseNew-ADOrganizationalUnit -Name "Groups" `-Path "ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion $Protect -verboseNew-ADOrganizationalUnit -Name "Admin" `-Path "ou=Groups,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion $Protect -verboseNew-ADOrganizationalUnit -Name "Desktops" `-Path "ou=Groups,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion $Protect -verboseNew-ADOrganizationalUnit -Name "User" `-Path "ou=Groups,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion $Protect -verboseNew-ADOrganizationalUnit -Name "Servers" `-Path "ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion $Protect -verboseNew-ADOrganizationalUnit -Name "PVS" `-Path "ou=Servers,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion $Protect -verboseNew-ADOrganizationalUnit -Name "XD76" `-Path "ou=Servers,ou=Lab,dc=$ADDomain,dc=$TLD" `-ProtectedFromAccidentalDeletion $Protect -verbose#Create AD security groupsNew-ADGroup -Name "LocalAdmins" -SamAccountName LocalAdmins `-GroupCategory Security -GroupScope Global `-DisplayName "Group for users who need local admin rights" `-Path "ou=Admin,ou=Groups,ou=Lab,dc=$ADDomain,dc=$TLD" `-Description "Group for users who need local admin rights" -verboseNew-ADGroup -Name "XDUsers" -SamAccountName XDUsers `-GroupCategory Security -GroupScope Global `-DisplayName "Group for users who need XenDesktop desktop access" `-Path "ou=User,ou=Groups,ou=Lab,dc=$ADDomain,dc=$TLD" `-Description "Group for users who need XenDesktop desktop access" -verbose#Create user accountsNew-ADUser -Name svc_ctxpvs -AccountPassword $CryptoPwd `-CannotChangePassword $True -ChangePasswordAtLogon $False `-Description "Citrix PVS Service Account" `-DisplayName "Citrix PVS Service Account" -Enabled $True `-PasswordNeverExpires $True `–Path "ou=Service,ou=Accounts,ou=Lab,dc=$ADDomain,dc=$TLD" `-SamAccountName "svc_ctxpvs" –UserPrincipalName "svc_ctxpvs@$ADDomain.$TLD" `-verboseNew-ADUser -Name svc_ctxsqldb -AccountPassword $CryptoPwd `-CannotChangePassword $True -ChangePasswordAtLogon $False `-Description "Citrix SQL DBA Service Account" `-DisplayName "Citrix SQL DBA Service Account" -Enabled $True `-PasswordNeverExpires $True `–Path "ou=Service,ou=Accounts,ou=Lab,dc=$ADDomain,dc=$TLD" `-SamAccountName "svc_ctxsqldb" –UserPrincipalName "svc_ctxsqldb@$ADDomain.$TLD" `-verboseNew-ADUser -Name User1 -AccountPassword $CryptoPwd `-CannotChangePassword $True -ChangePasswordAtLogon $False `-Description "User1 PvD" `-DisplayName "User1" -Enabled $True `-PasswordNeverExpires $True `–Path "ou=User,ou=Accounts,ou=Lab,dc=$ADDomain,dc=$TLD" `-SamAccountName "User1" –UserPrincipalName "User1@$ADDomain.$TLD" `-verboseNew-ADUser -Name User2 -AccountPassword $CryptoPwd `-CannotChangePassword $True -ChangePasswordAtLogon $False `-Description "User2 PvD" `-DisplayName "User2" -Enabled $True `-PasswordNeverExpires $True `–Path "ou=User,ou=Accounts,ou=Lab,dc=$ADDomain,dc=$TLD" `-SamAccountName "User2" –UserPrincipalName "User2@$ADDomain.$TLD" `-verboseNew-ADUser -Name User3 -AccountPassword $CryptoPwd `-CannotChangePassword $True -ChangePasswordAtLogon $False `-Description "User3 PvD" `-DisplayName "User3" -Enabled $True `-PasswordNeverExpires $True `–Path "ou=User,ou=Accounts,ou=Lab,dc=$ADDomain,dc=$TLD" `-SamAccountName "User3" –UserPrincipalName "User3@$ADDomain.$TLD" `-verbose#all users in the Lab/Accounts/User OU get added to the XDUsers security group$Users = get-aduser `-searchbase "ou=user,ou=accounts,ou=lab,dc=$ADDomain,dc=$tld" `-filter *Add-ADGroupMember -Identity XDUsers -Members $Users#any user in the Lab/Accounts/User OU that has PvD in the description#gets added to the LocalAdmins security group$Users = get-aduser `-searchbase "ou=user,ou=accounts,ou=lab,dc=$ADDomain,dc=$tld" `-filter 'Description -like "*PvD*"'Add-ADGroupMember -Identity LocalAdmins -Members $Users#Create AD computer accountsNew-ADComputer -Name PVS76 -SamAccountName PVS76 -Description "PVS76" `-Path "ou=PVS,ou=Servers,ou=Lab,dc=$ADDomain,dc=$TLD" -Enabled $True -verboseNew-ADComputer -Name XD76 -SamAccountName XD76 -Description "XD76" `-Path "ou=XD76,ou=Servers,ou=Lab,dc=$ADDomain,dc=$TLD" -Enabled $True -verboseNew-ADComputer -Name Director -SamAccountName Director -Description "Director" `-Path "ou=XD76,ou=Servers,ou=Lab,dc=$ADDomain,dc=$TLD" -Enabled $True -verboseNew-ADComputer -Name StoreFront -SamAccountName StoreFront -Description "StoreFront" `-Path "ou=XD76,ou=Servers,ou=Lab,dc=$ADDomain,dc=$TLD" -Enabled $True -verboseNew-ADComputer -Name SQL -SamAccountName SQL -Description "SQL" `-Path "ou=XD76,ou=Servers,ou=Lab,dc=$ADDomain,dc=$TLD" -Enabled $True -verbose |
I named the script CreateLab.ps1.
Figure 1 shows my Active Directory structure before running the script.
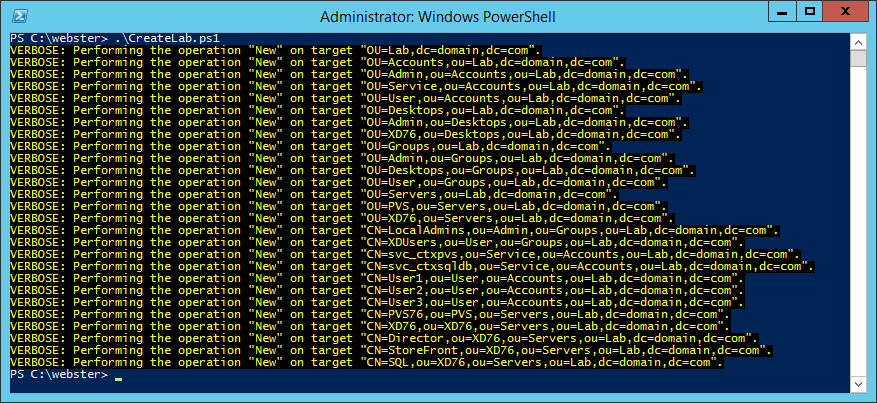
Figure 2 shows the results of running the PowerShell script.
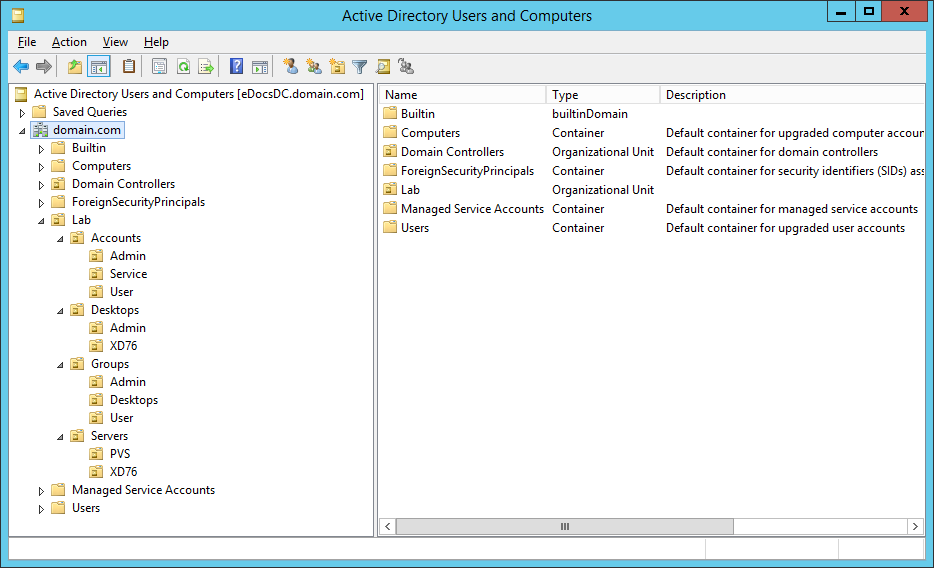
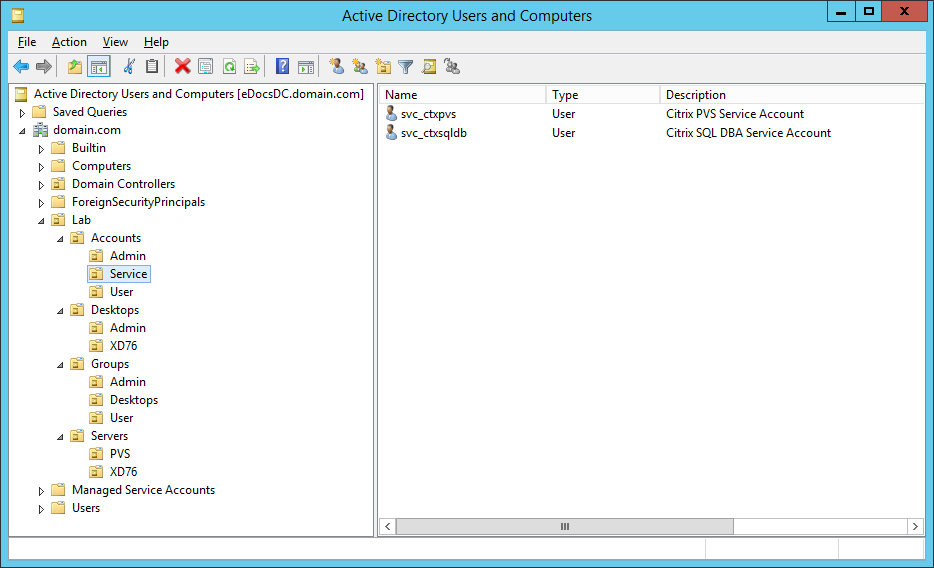
Figures 3 through 13 show the AD structure after running the script (which matches running the batch file).
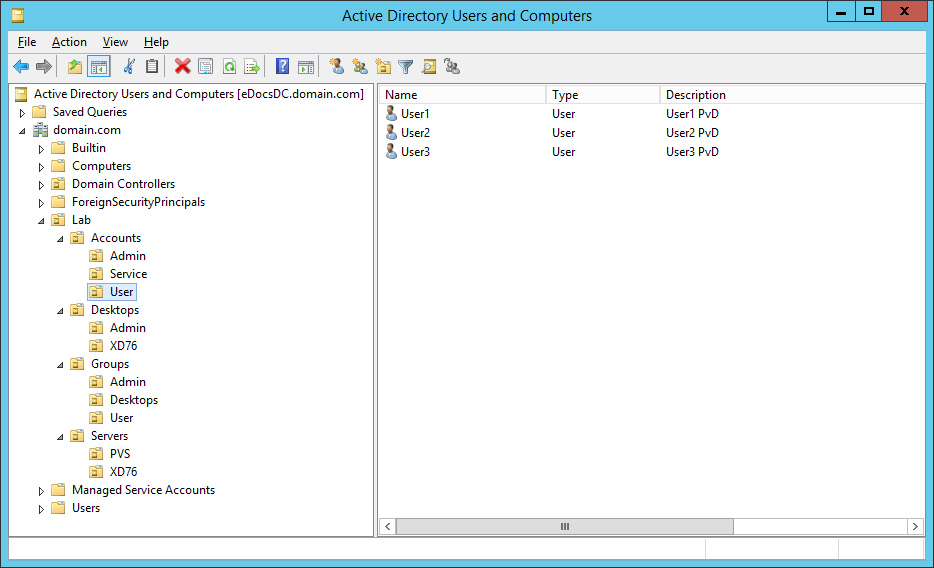
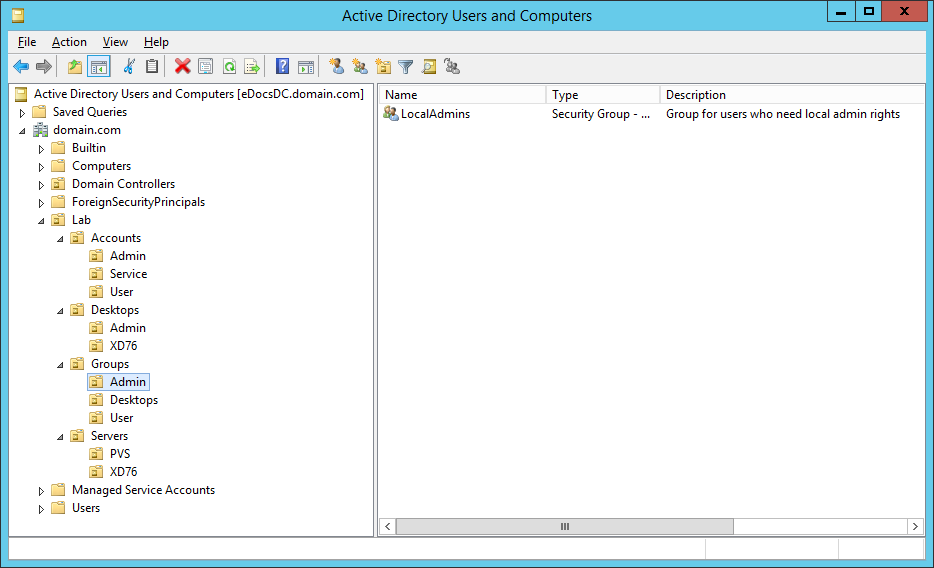
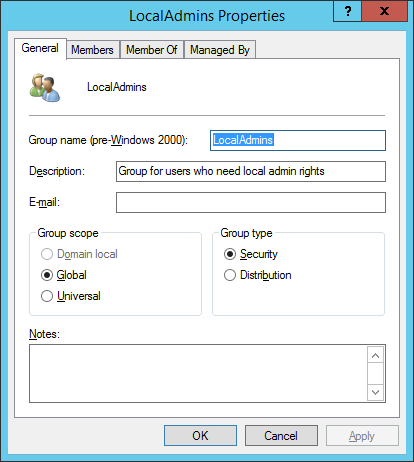
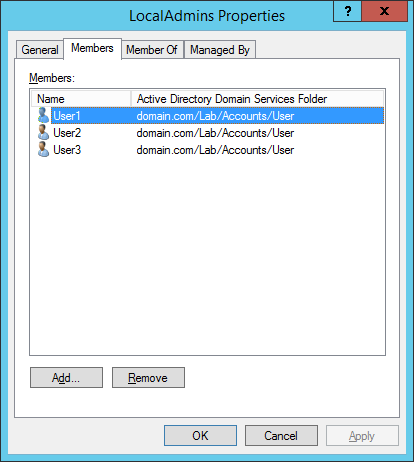
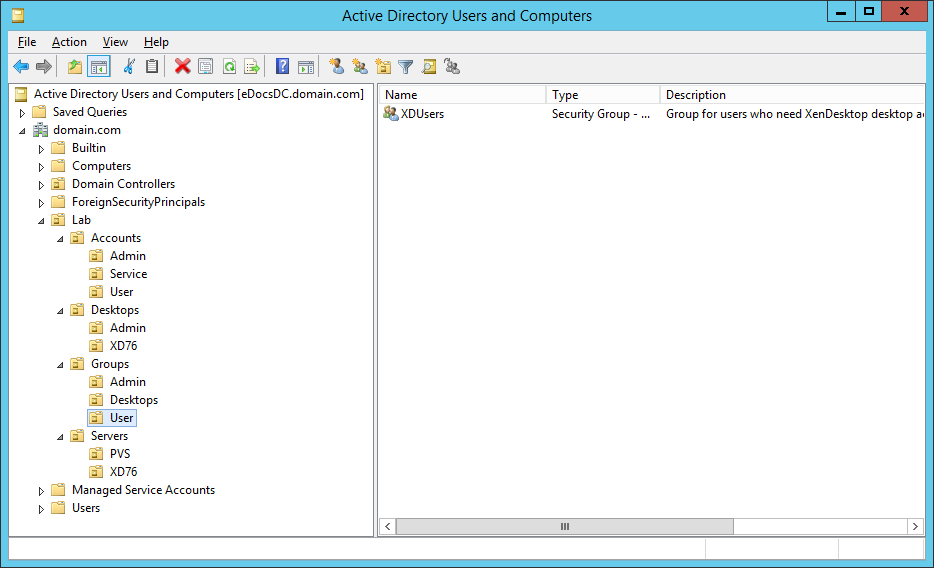
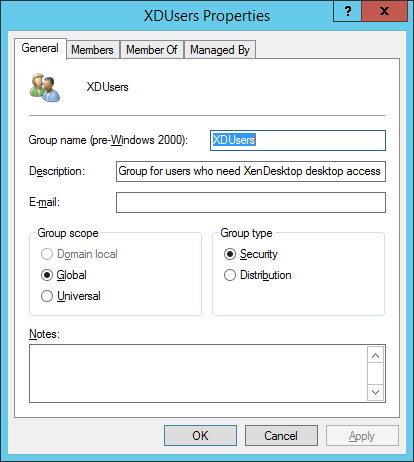
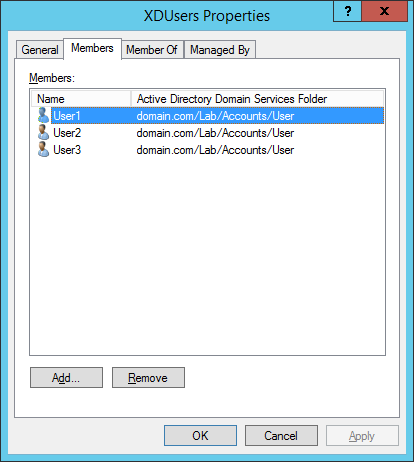
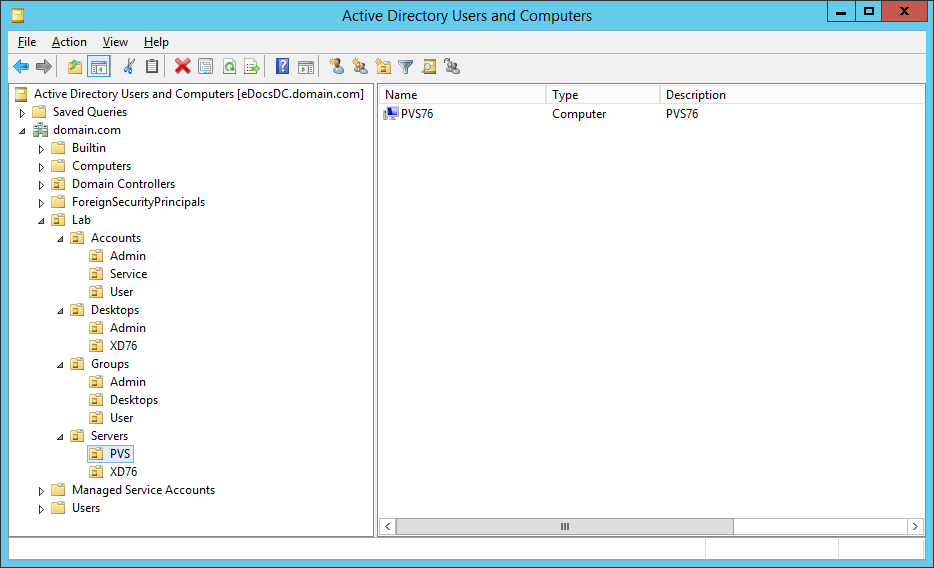
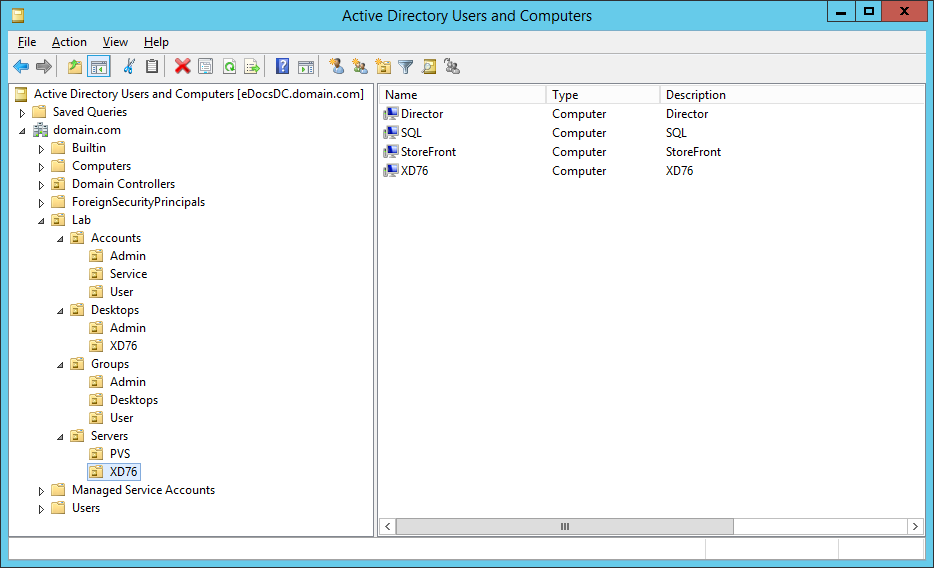
There you go, a PowerShell version of the batch file I use to create my lab’s AD structure.
You can get a PS1 version here and a TXT version here.
Thanks
Webster
Carl,
I didn’t mean for you to burn your free time to convert the batch file to PS!!! Cool that you provided the PS script to accomplish the same as the batch file. I intend to test this sucker out.
Thanks for providiing your knowledge…always a great resource.
Rob
Only took an hour to do it.
Webster