At a customer site recently, I needed a way to list all the Enabled Windows Firewall Inbound Rules. I could not get what I needed by using the Windows
1 | netsh advfirewall monitor show firewall rule name=all dir=in |
command so I turned to using PowerShell.
I found the following article by James O’Neill that helped me get started.
What I needed for a headstart was the following code from James’ article:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 | Function Get-FireWallRule{Param ($Name, $Direction, $Enabled, $Protocol, $profile, $action, $grouping)$Rules=(New-object –comObject HNetCfg.FwPolicy2).rulesIf ($name) {$rules= $rules | where-object {$_.name -like $name}}If ($direction) {$rules= $rules | where-object {$_.direction -eq $direction}}If ($Enabled) {$rules= $rules | where-object {$_.Enabled -eq $Enabled}}If ($protocol) {$rules= $rules | where-object {$_.protocol -eq $protocol}}If ($profile) {$rules= $rules | where-object {$_.Profiles -bAND $profile}}If ($Action) {$rules= $rules | where-object {$_.Action -eq $Action}}If ($Grouping) {$rules= $rules | where-object {$_.Grouping -like $Grouping}}$rules}Get-firewallRule -enabled $true | sort direction,applicationName,name |format-table -wrap -autosize -property Name, @{Label=”Action”; expression={$Fwaction[$_.action]}},@{label="Direction";expression={ $fwdirection[$_.direction]}},@{Label="Protocol"; expression={$FwProtocols[$_.protocol]}} , localPorts,applicationname |
I created a script named listfw.ps1 and when I ran the script, I received the output shown in Figure 1.
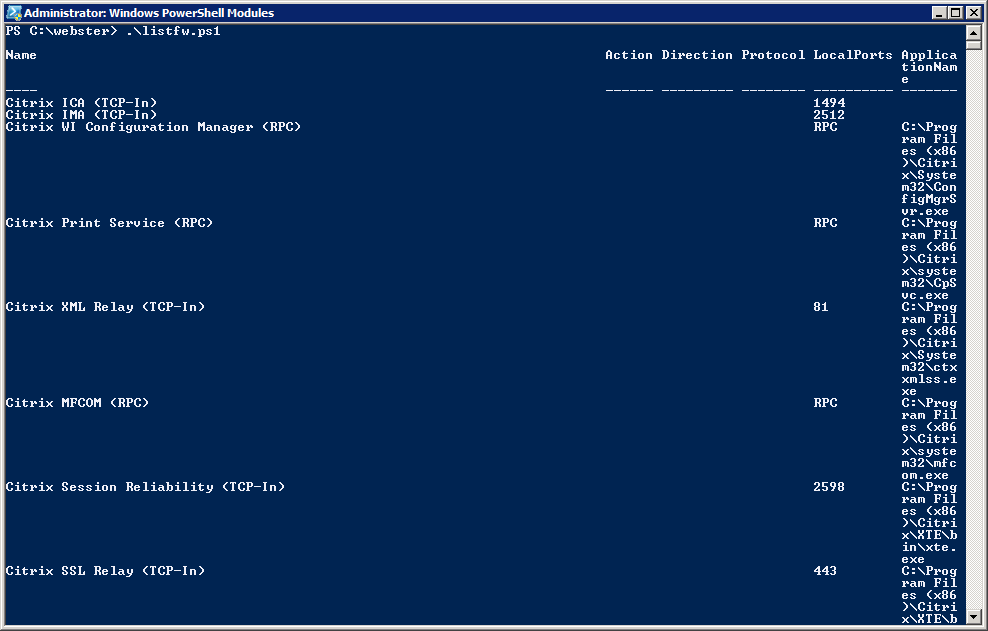
The last column wasn’t formatted properly for me so I thought maybe the “–wrap” parameter of Format-Table was causing the issue. So I removed the “-wrap” and reran the script. I received the output shown in Figure 2.
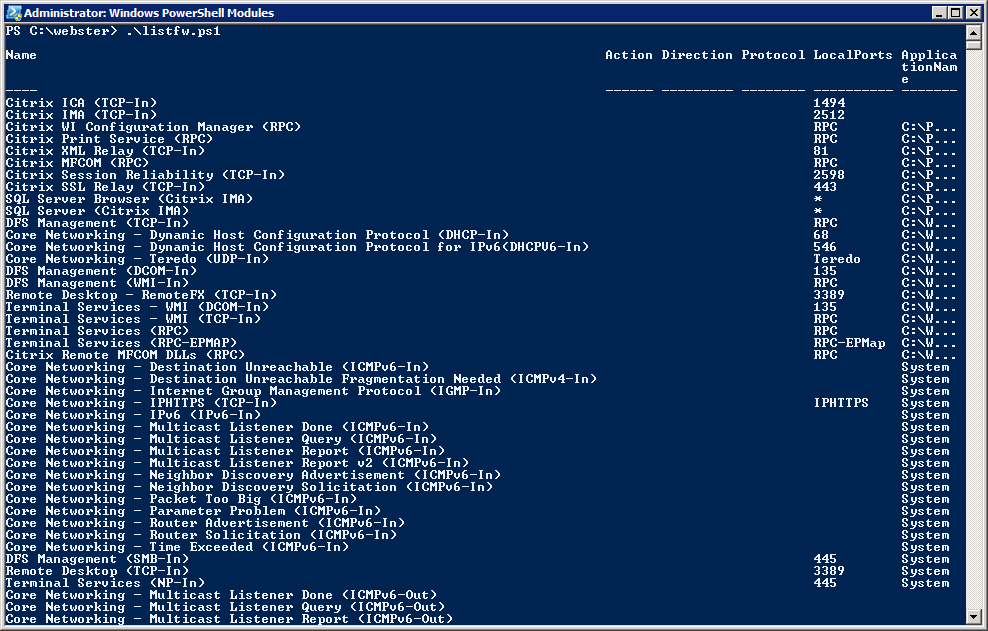
OK, still not what I need. So I thought maybe the “-autosize” was the culprit. I removed the “-autosize” and reran the script. I received the output shown in Figure 3.
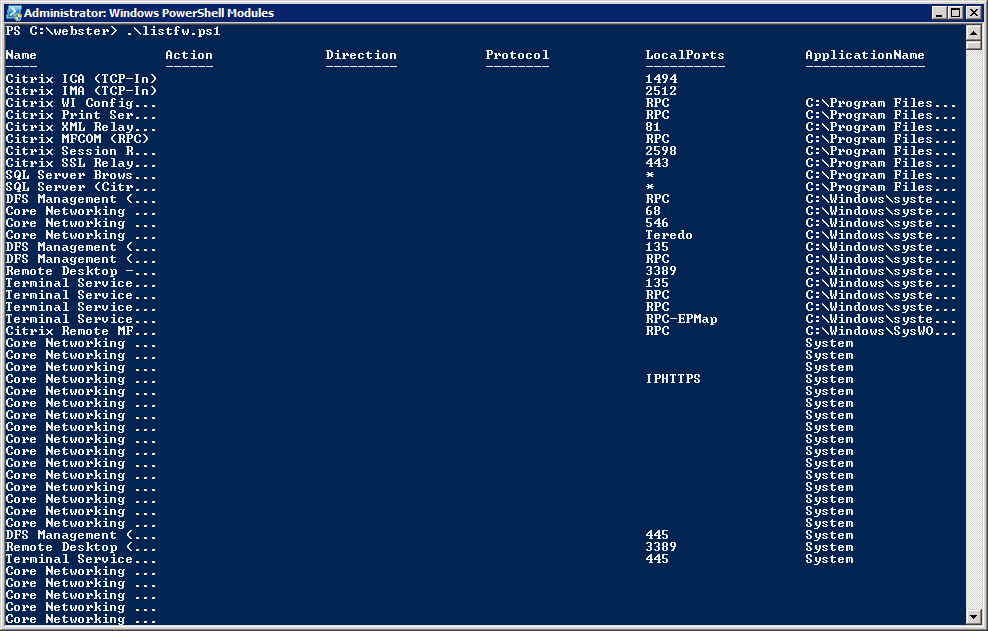
OK, I am getting further away from what I really. What I want is a way for the Name column and the ApplicationName column to be full width.
Using get-help format-table –full gave me a clue. The “-property” parameter has some options available:
1 2 3 4 5 | -- Name (or Label) <string>-- Expression <string> or <script block>-- FormatString <string>-- Width <int32>-- Alignment (value can be "Left", "Center", or "Right") |
I can see in Jame’s original code he is using the “Label” and “Expression” options. I just need to figure out how to use the “Width” option. After much trial and error, I came up with the following code:
1 2 3 4 5 6 7 8 9 10 | $spaces1 = " " * 71$spaces2 = " " * 64Get-firewallRule -enabled $true | sort name | `format-table -property `@{label="Name" + $spaces1 ; expression={$_.name} ; width=75}, `@{label="Action" ; expression={$Fwaction[$_.action]} ; width=6 }, `@{label="Direction" ; expression={$fwdirection[$_.direction]} ; width=9 }, `@{label="Protocol" ; expression={$FwProtocols[$_.protocol]} ; width=8 }, `@{label="Local Ports" ; expression={$_.localPorts} ; width=11}, `@{label="Application Name" + $spaces2 ; expression={$_.applicationname} ; width=80} |
Running the script gives me the output shown in Figure 4.
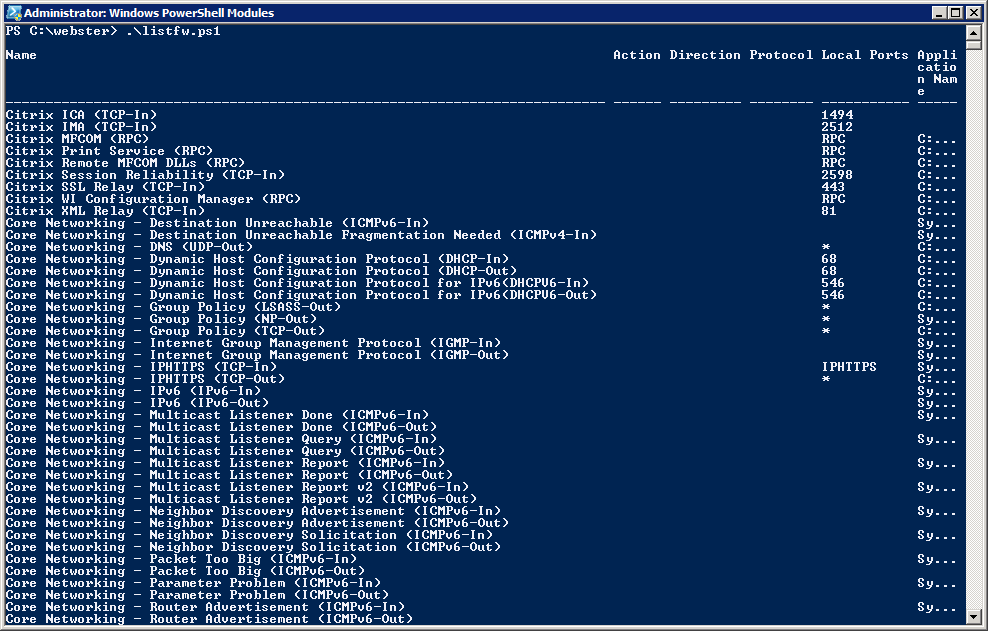
DOH! So close. It seems the output is now limited by the width of the screen. Looking at the help for Get-Table, I cannot see any option that allows me to make the table wider. That led me to find this article.
http://poshoholic.com/2010/11/11/powershell-quick-tip-creating-wide-tables-with-powershell/
It appears the solution is very simple. Use out-string –width nnn. Using a width of 200 and running the following command, I get what is shown below.
1 | .\listfw.ps1 | out-string –width 200 | out-file .\fw.txt |
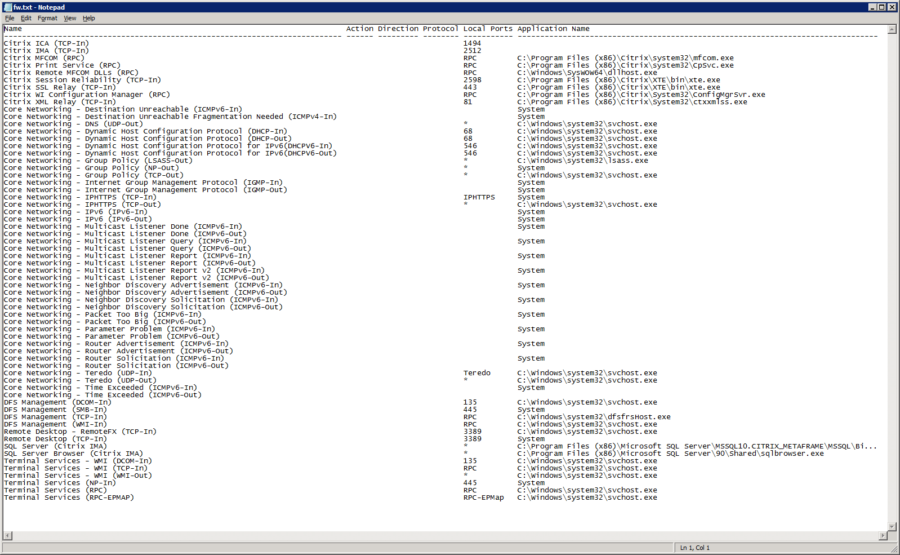
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 | Name Action Direction Protocol Local Ports Application Name--------------------------------------------------------------------------- ------ --------- -------- ----------- --------------------------------------------------------------------------------Citrix ICA (TCP-In) 1494Citrix IMA (TCP-In) 2512Citrix MFCOM (RPC) RPC C:\Program Files (x86)\Citrix\system32\mfcom.exeCitrix Print Service (RPC) RPC C:\Program Files (x86)\Citrix\system32\CpSvc.exeCitrix Remote MFCOM DLLs (RPC) RPC C:\Windows\SysWOW64\dllhost.exeCitrix Session Reliability (TCP-In) 2598 C:\Program Files (x86)\Citrix\XTE\bin\xte.exeCitrix SSL Relay (TCP-In) 443 C:\Program Files (x86)\Citrix\XTE\bin\xte.exeCitrix WI Configuration Manager (RPC) RPC C:\Program Files (x86)\Citrix\System32\ConfigMgrSvr.exeCitrix XML Relay (TCP-In) 81 C:\Program Files (x86)\Citrix\System32\ctxxmlss.exeCore Networking - Destination Unreachable (ICMPv6-In) SystemCore Networking - Destination Unreachable Fragmentation Needed (ICMPv4-In) SystemCore Networking - DNS (UDP-Out) * C:\Windows\system32\svchost.exeCore Networking - Dynamic Host Configuration Protocol (DHCP-In) 68 C:\Windows\system32\svchost.exeCore Networking - Dynamic Host Configuration Protocol (DHCP-Out) 68 C:\Windows\system32\svchost.exeCore Networking - Dynamic Host Configuration Protocol for IPv6(DHCPV6-In) 546 C:\Windows\system32\svchost.exeCore Networking - Dynamic Host Configuration Protocol for IPv6(DHCPV6-Out) 546 C:\Windows\system32\svchost.exeCore Networking - Group Policy (LSASS-Out) * C:\Windows\system32\lsass.exeCore Networking - Group Policy (NP-Out) * SystemCore Networking - Group Policy (TCP-Out) * C:\Windows\system32\svchost.exeCore Networking - Internet Group Management Protocol (IGMP-In) SystemCore Networking - Internet Group Management Protocol (IGMP-Out) SystemCore Networking - IPHTTPS (TCP-In) IPHTTPS SystemCore Networking - IPHTTPS (TCP-Out) * C:\Windows\system32\svchost.exeCore Networking - IPv6 (IPv6-In) SystemCore Networking - IPv6 (IPv6-Out) SystemCore Networking - Multicast Listener Done (ICMPv6-In) SystemCore Networking - Multicast Listener Done (ICMPv6-Out)Core Networking - Multicast Listener Query (ICMPv6-In) SystemCore Networking - Multicast Listener Query (ICMPv6-Out)Core Networking - Multicast Listener Report (ICMPv6-In) SystemCore Networking - Multicast Listener Report (ICMPv6-Out)Core Networking - Multicast Listener Report v2 (ICMPv6-In) SystemCore Networking - Multicast Listener Report v2 (ICMPv6-Out)Core Networking - Neighbor Discovery Advertisement (ICMPv6-In) SystemCore Networking - Neighbor Discovery Advertisement (ICMPv6-Out)Core Networking - Neighbor Discovery Solicitation (ICMPv6-In) SystemCore Networking - Neighbor Discovery Solicitation (ICMPv6-Out)Core Networking - Packet Too Big (ICMPv6-In) SystemCore Networking - Packet Too Big (ICMPv6-Out)Core Networking - Parameter Problem (ICMPv6-In) SystemCore Networking - Parameter Problem (ICMPv6-Out)Core Networking - Router Advertisement (ICMPv6-In) SystemCore Networking - Router Advertisement (ICMPv6-Out)Core Networking - Router Solicitation (ICMPv6-In) SystemCore Networking - Router Solicitation (ICMPv6-Out)Core Networking - Teredo (UDP-In) Teredo C:\Windows\system32\svchost.exeCore Networking - Teredo (UDP-Out) * C:\Windows\system32\svchost.exeCore Networking - Time Exceeded (ICMPv6-In) SystemCore Networking - Time Exceeded (ICMPv6-Out)DFS Management (DCOM-In) 135 C:\Windows\system32\svchost.exeDFS Management (SMB-In) 445 SystemDFS Management (TCP-In) RPC C:\Windows\system32\dfsfrsHost.exeDFS Management (WMI-In) RPC C:\Windows\system32\svchost.exeRemote Desktop - RemoteFX (TCP-In) 3389 C:\Windows\system32\svchost.exeRemote Desktop (TCP-In) 3389 SystemSQL Server (Citrix IMA) * C:\Program Files (x86)\Microsoft SQL Server\MSSQL10.CITRIX_METAFRAME\MSSQL\Bi...SQL Server Browser (Citrix IMA) * C:\Program Files (x86)\Microsoft SQL Server\90\Shared\sqlbrowser.exeTerminal Services - WMI (DCOM-In) 135 C:\Windows\system32\svchost.exeTerminal Services - WMI (TCP-In) RPC C:\Windows\system32\svchost.exeTerminal Services - WMI (WMI-Out) * C:\Windows\system32\svchost.exeTerminal Services (NP-In) 445 SystemTerminal Services (RPC) RPC C:\Windows\system32\svchost.exeTerminal Services (RPC-EPMAP) RPC-EPMap C:\Windows\system32\svchost.exe |
Now I have a report I can use. I can run this script before and after installing XenApp 6.5 and see what changes were made to the Windows Firewall rules.
This is awesome but it only shows locally created Firewall Rules, it doesn’t list any GPO applied.
Correct. The HNetCfg.FWPolicy2 comObject only contains the local firewall rules. Starting with Windows 8 and Serer 2012, you now have the Get-NetFirewallRule cmdlet that has a lot more features.
Thanks
Webster
If you pipe the output to the “Export-Csv” option instead of the “Format-Table” option, you get all characters in each column without any loss. Then you can simply open it in your favourite CSV program.
https://technet.microsoft.com/en-us/library/hh849932.aspx
HTH